jtsec, Blog
Par un écrivain mystérieux
Description
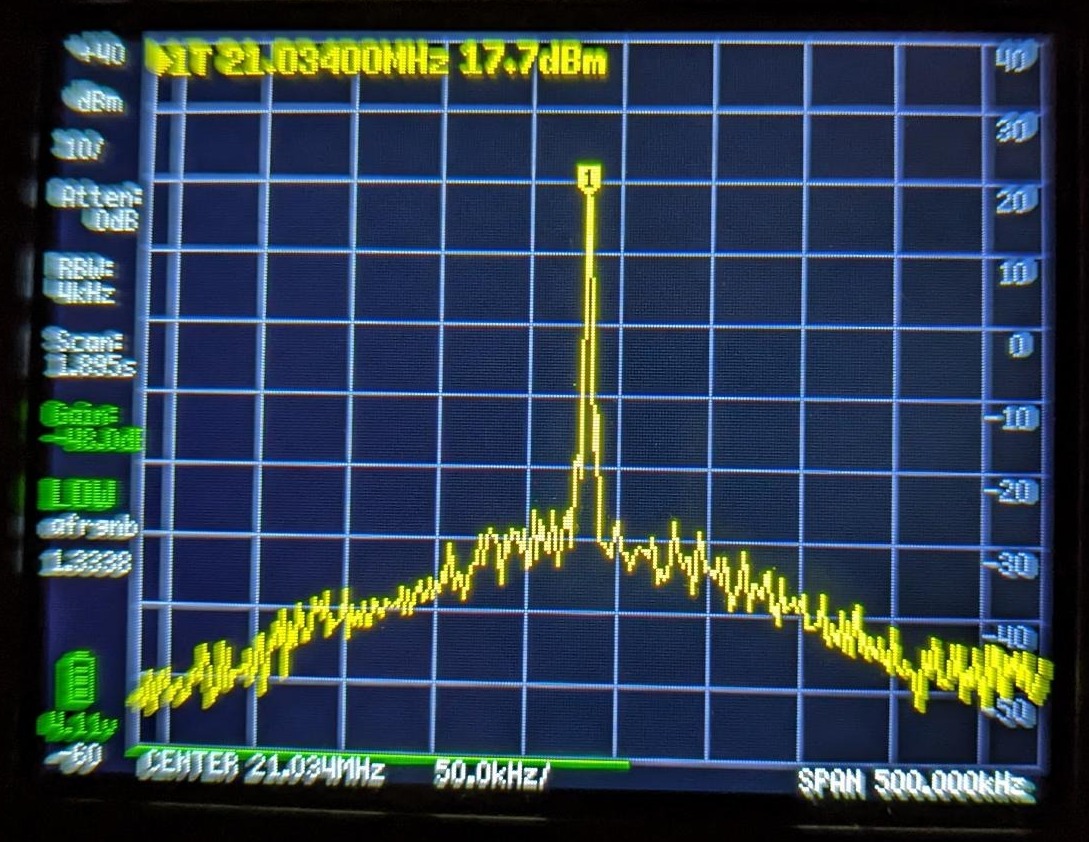
While performing a STIC evaluation of a product, the evaluation team at jtsec thought that it would be interesting to analyze the communications between two embedded devices that were part of the product. The main objective was to determine whether those communications were properly secured with encryption and other important security measures when it comes to devices that communicate using radio frequencies such as protection against jamming, GPS spoofing or replay attacks.

jtsec Beyond IT Security on LinkedIn: jtsec, Blog

jtsec Beyond IT Security on LinkedIn: jtsec, Blog

Antonio Cortes on LinkedIn: jtsec, Blog
auto_ignore>no not working!!! · Issue #1081 · ossec

jtsec Beyond IT Security on X: Ser el primer laboratorio en

jtsec, Blog

JTSEC - Crunchbase Company Profile & Funding

Cybertech Information Systems

jtsec, Blog

jtsec, Blog

jtsec Blog about computer security, sharing jtsec thoughts

jtsec, Blog
depuis
par adulte (le prix varie selon la taille du groupe)