A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory
Par un écrivain mystérieux
Description
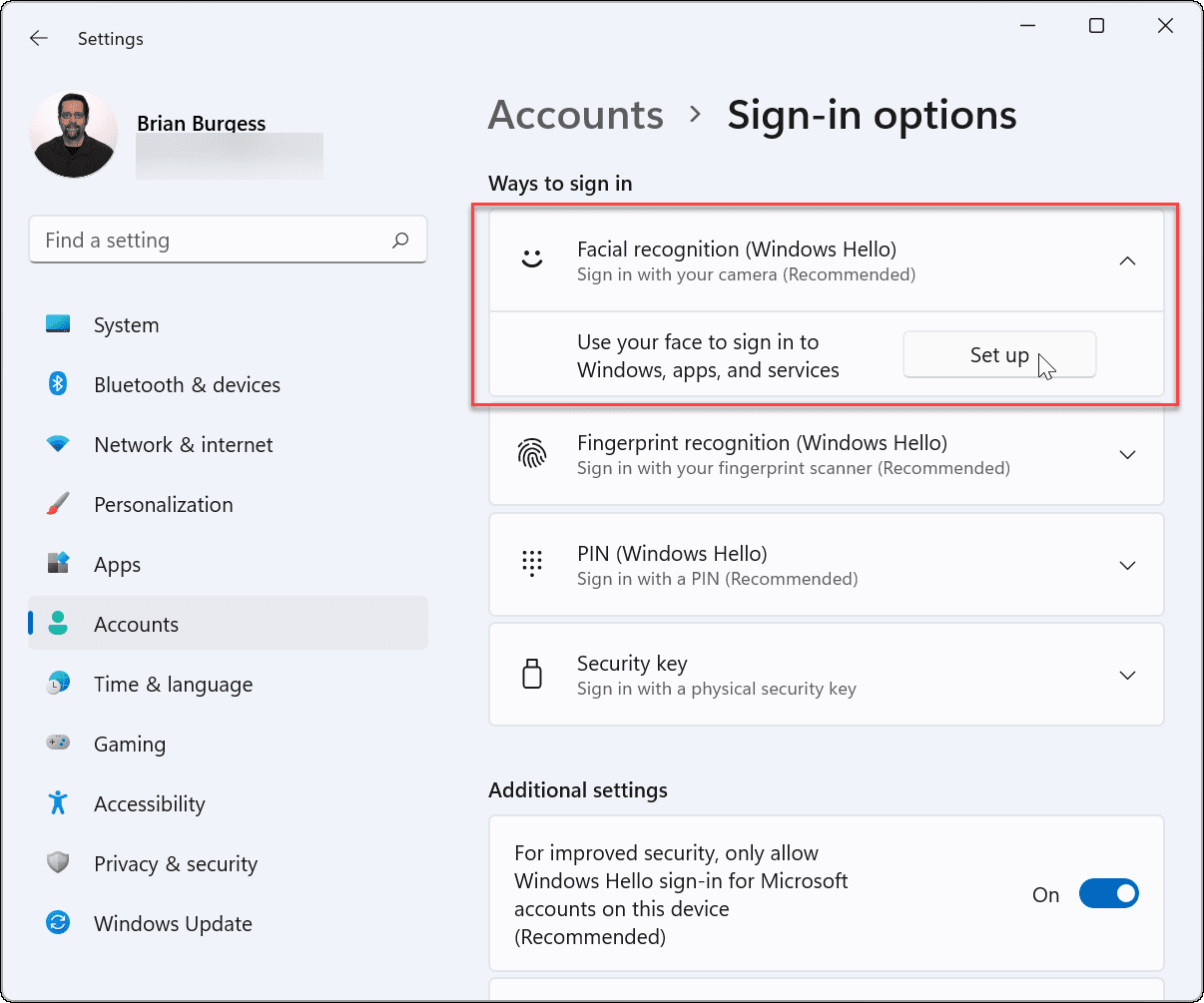
Client-side Login Procedures With protocol analysis, we figure out what data is exchanged between the client and the server for Windows Hello login. Now we’d like to know where is authentication data stored in the client-side? And how authentication data is used to? For these, we performed static and dynamic debugging for login-related services on … Continue reading A Deep Dive into Windows Hello (2) →
ULTIMATE HACKER SUMMER CAMP — Part Five: DEFCON Safe Mode, by DCG 201

The Hacker Playbook 2 - Practical Guide To Penetration Testing

A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory

Live Demo: Hack your first computer with Immersive Labs

The Hacked World Order Council on Foreign Relations

Hacking with Ease: Pass the Hash Attack Made Simple with CrackMapExec, by Jinendar Kothari
What about Linux is needed to be known to become an ethical hacker, and why? - Quora
/cdn.vox-cdn.com/uploads/chorus_asset/file/25104383/windowshellofingerprint.jpg)
Microsoft's Windows Hello fingerprint authentication has been bypassed - The Verge

HPE SimpliVity Technical Deep Dive and Demo - Storcom, Lombard, Illinois, United States of America
MSAB Frontline Solutions - Forensic Focus

Bypassing Windows Hello Without Masks or Plastic Surgery

Game of Tokens: AD post exploitation with Token Impersonation, by Jinendar Kothari
depuis
par adulte (le prix varie selon la taille du groupe)